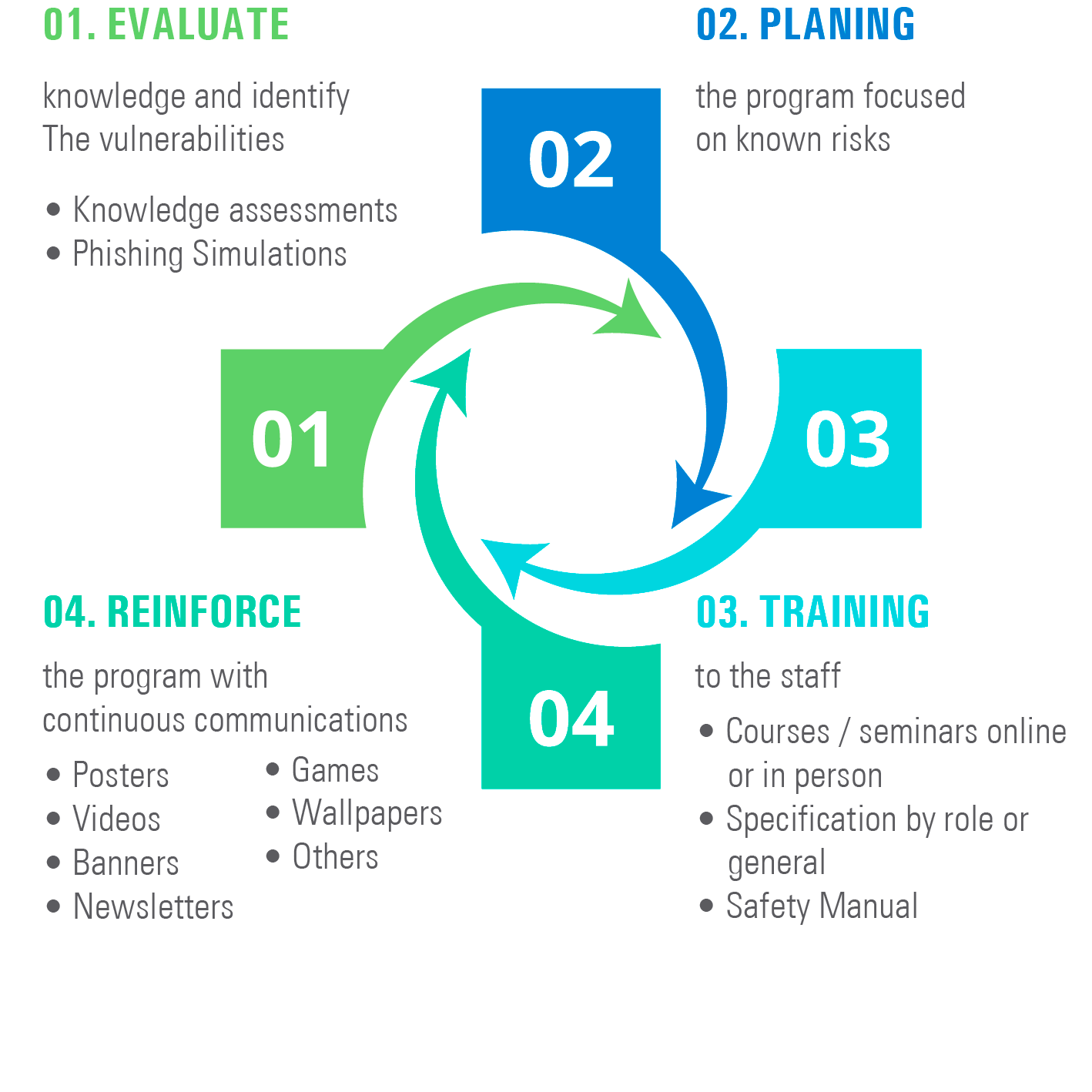
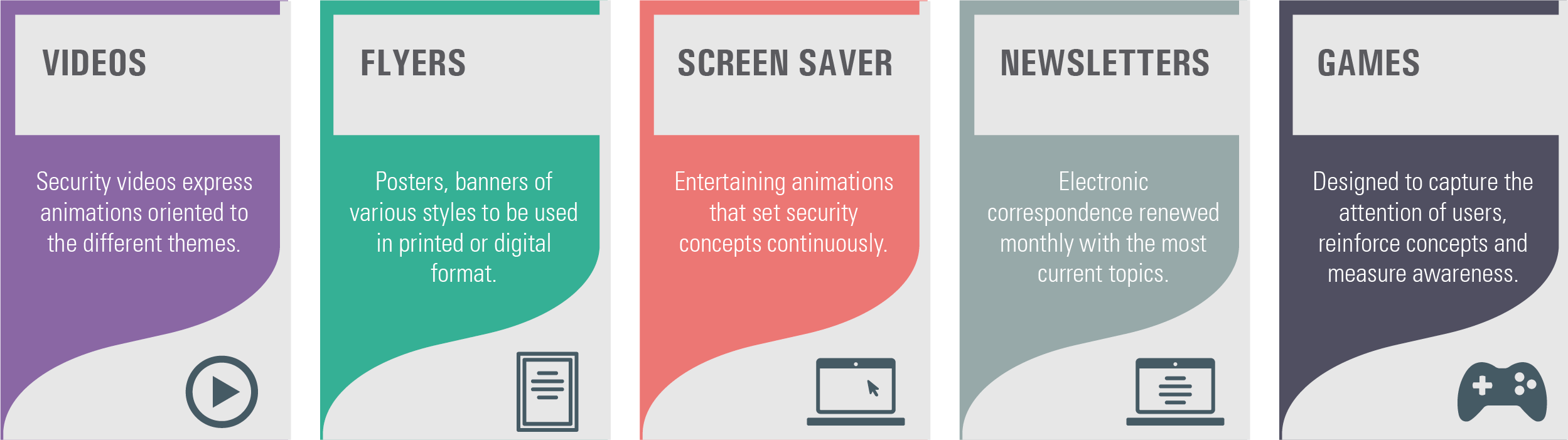
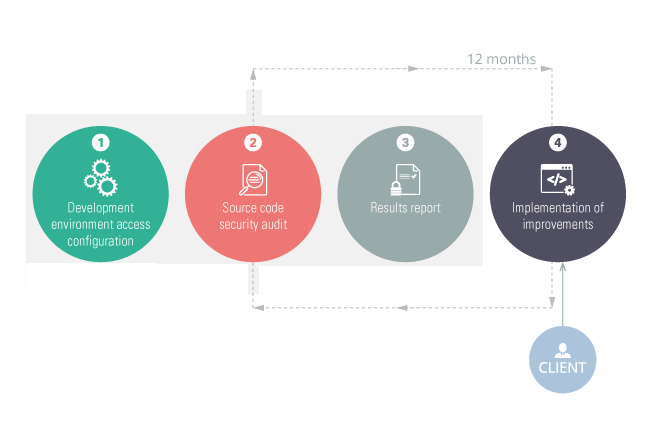
Security continues
ACC: Adoption to Cloud Computing
Many organizations have made the strategic decision to migrate to the cloud, in order to take advantage of the many benefits of Cloud Computing, however, not always have the time and experience to face the new paradigm in an efficient and successful. A great challenge facing infrastructure leaders is to identify the most appropriate Cloud Computing offerings according to the needs of the company and the objectives it defines for its services, requiring specialization in the different areas of the new paradigm . Although the concept of cloud is associated with the ease and simplification of the traditional infrastructure problem, this will be true to the extent that in each of the stages decisions are made that benefit the organization, overturning the myth that The cloud are virtual machines on powerful servers.
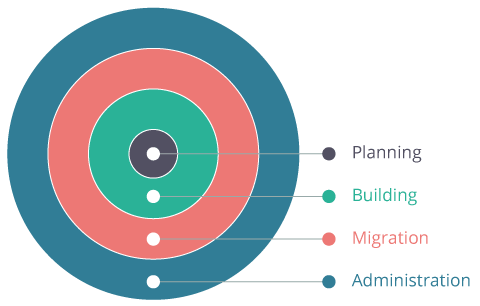
Adoption Model
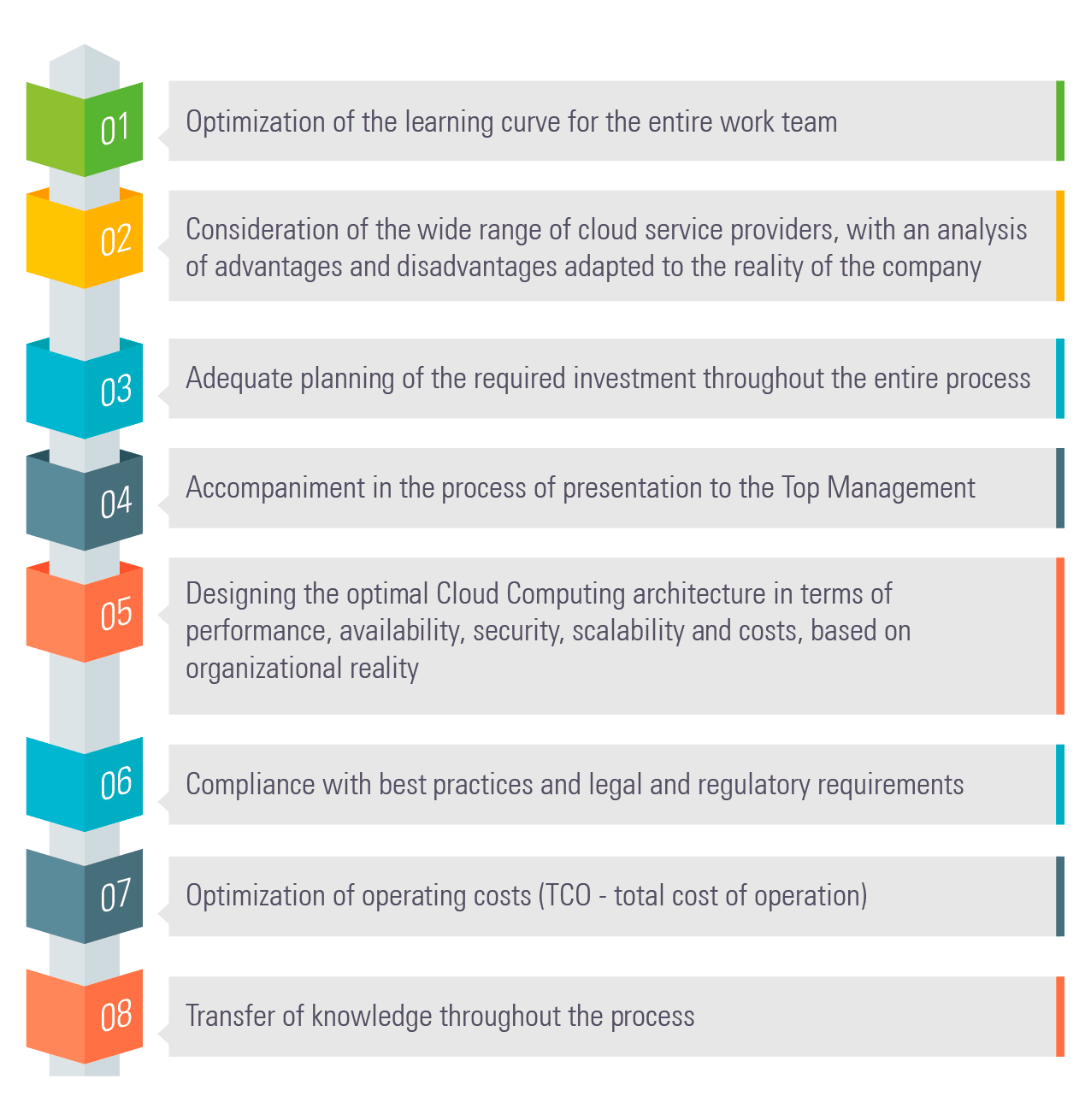
Benefits
Main issues
- Which providers could provide cloud services aligned with business requirements?
- What limitations are there in migration and how can it be minimized?
- How to present the migration project against non-technical decisions?
- What is the best deployment model? Private | Public | Hybrid | Community
- What service models do you choose? IaaS | PaaS | SaaS
- What services do you use for processing, storage, database, networking, development,
administration, security, analysis, …?
- Microsoft Azure: Web site | Virtual Machines| Mobile Services | Cloud Services | Storage | Multimedia Services | ...
- Amazon: AWS EC2| EC2 Container Service | Elastice Beanstalk | Lambda | ...
- Office 365
- G Suite - What is your optimal architecture?
- How to minimize the likelihood of hidden costs (not initially considered)?
- How to adapt the operational processes of administration and operation to the new paradigm?
- What type of training does the internal staff require according to their new role?
Frameworks
-

ISO/IEC 17788 (Information technology -- Cloud computing -- Overview and vocabulary)
-
ISO/IEC 17789 (Information technology -- Cloud computing -- Reference architecture)
-
ISO/IEC 19086-1 (Information technology -- Cloud computing -- Service level agreement (SLA) framework -- Part 1: Overview and concepts)
-
ISO/IEC 27017 (Information technology -- Security techniques -- Code of practice for information security controls based on ISO/IEC 27002 for cloud services)
-
ISO/IEC 27018 (Information technology -- Security techniques -- Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors)
-

NIST Cloud Computing Program
-

Security Guidance for Critical Areas of Focus in Cloud Computing
-
Cloud Computing Adoption Framework–a security framework for business clouds
Cloud Computing Adoption Model